In this series of articles, we will cover a number of topics around security
1. What is really going on?
2. Why is this happening?
3. Who are they?
4. What are the different types of threats?
5. What can you do about it?
Part 2 - Why is this happening and why is the security discussion different now?
In the second part of the series, in this article, we cover the key 6 reasons this happening and why you should be looking at security differently.
1. Availability of Hacking Software - “There's an app for that”
One of the biggest differences is that readily available amounts of cheap malicious code and apps that were unattainable or unaffordable in years gone by.
As an example for even as little as $7, cybercriminals can get their hands on the Russian password-stealing tool that steals information from web browsers. https://www-forbes-com.cdn.amp...-bottom-pricing/amp/
Shodan is the world's first search engine for Internet-connected devices. https://www.shodan.io/explore/tag/printer
2. It is now much easier to train as a hacker - “there's a class for that”
As an example, Cybercriminals can take a class on stealing credit cards http://money.cnn.com/2017/07/1...l-shadows/index.html
And worth a mention, that for the White Hat Hacker (Good Guys) there is a CompTIA security cert https://amp.thehackernews.com/...online-training.html
3. HAAS - You do it for me
If you don’t want to wait or do learn you easily hire a hacker, yes, that’s right, as part of Everything as a Service, you can now pretty much get literally everything and so Haas Hacking as a service is a thing now.
As an example for $8 you can get Crypting services to hide malware http://uk.businessinsider.com/...-account-access-90-5
$5 for DDoS-as-service (distributed denial of service) designed to overwhelm a server/website or another network resource through sheer volume of messages, connections, or packets to causes it to grind to a halt or crash thereby denying services to legitimate users.
DDoS as service prices are also tumbling. Hemant Jain, vice president of engineering for security company Fortinet, said that he has found providers who are selling an hour of DDoS for $5, a 24-hour day of it for $40 and a week for $260. http://www.cutimes.com/2013/05...for-hire-on-the-rise
For $7 anyone can spread malware and cause serious damage http://news.softpedia.com/news...ernight-517013.shtml
Ransomware will encrypt your file until you pay a ransom
There are more powerful hacking tools to use, like scrapers, browsers and
Phishing-as-a-Service (PhaaS) platform that offers low cost, "automated solution for the beginner scammers," allowing them to trick people into handing over their credentials. http://thehackernews.com/2017/...-as-service.html?m=1
4. The rewards can be huge
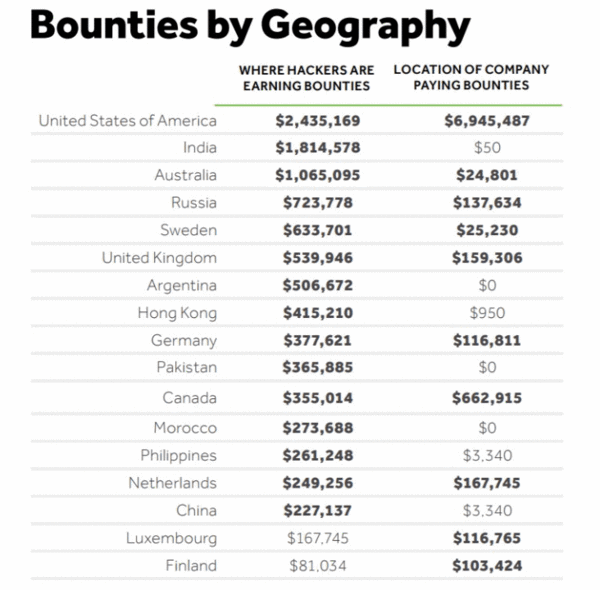
Rewards - Through May 2017, organizations have awarded hackers over $17 million in bounties on HackerOne, and over $7 million awarded in 2016 alone. o https://www.hackerone.com/site...ecurity%20Report.pdf
Even something published the below example of phishing as a joke but were surprised by the high number gullible responses.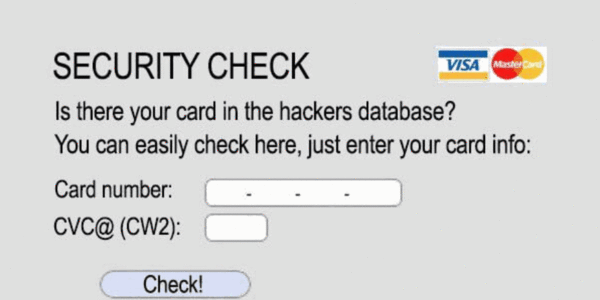

Black Market values
- A complete medical record – $1,000 more if used for bribery or to sell on to insurance companies.
- Credit card details :-
· $5 to $30 in the US per person in the US,
· $20 to $35 in the UK
· $20 to $40 in Canada
· $21 to $40 in Australia
· $25 to $45 in the European Union
- Driver’s license - $20
- Netflix password - $3.05
- Spotify passwords - $2.80
- Email addresses - $2.29
- Bank login credentials :-
· for a $2,200 balance bank account: $190
· from $500 for a $6,000 account balance, to $1,200 for a $20,000 account balance
· from $700 for a $10,000 account balance, to $900 for a $16,000 account balance
- Login credentials for online payment services such as PayPal: between $20 and $50 for account balances from $400 to $1,000; between $200 and $300 for balances from $5,000 to $8,000
- Login credentials to hotel loyalty programs and online auction accounts: $20 to $1,400
- Login credentials for online premium content services such as Netflix: as little as $0.55
http://www.thisismoney.co.uk/m...it-card-details.html
White hat hackers who help companies through bounty programs can also make money by finding flaws and flagging them to the companies involved, who encourage the white hat hackers by paying bounties.
5. The number of devices out there
According to Gartner, in 2020, 25 Billion Connected "Things" Will Be in Use (up from 4.9 Billion in 2015)
There are more connected devices out there for you to connect to, IOT, fridges, ovens, Segways, even seagoing ship.
It's also scary what can be done with these connected devices now that it possible to blend the cyber and physical worlds with hacking with cyberweapons like the Stuxnet virus that attacked Iran's Natanz nuclear facility by causing centrifuges to spin out of control. http://www.businessinsider.com...thought-2013-11?IR=T
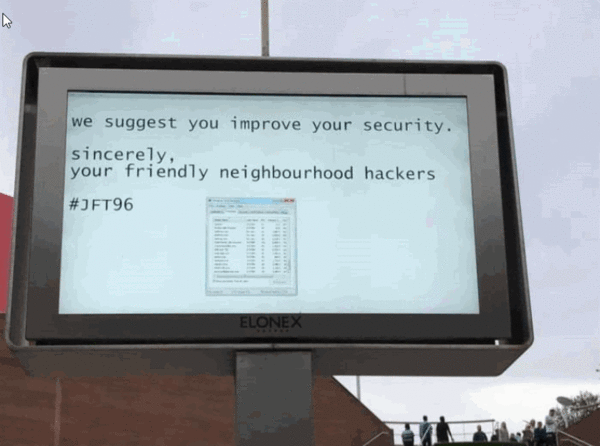
If you were not sure what I meant about a seagoing ship, this is a 2017 tweet from a hacker.
x0rz @x0rz Duuuuuude, default creds everywhere. I'm connected to a ship as admin right now. Hacking ships is easy pic.twitter.com/UmLPIveTa 10:31 AM - 18 Jul 2017
And this article shows https://thenextweb-com.cdn.amp...-hackable-now/?amp=1
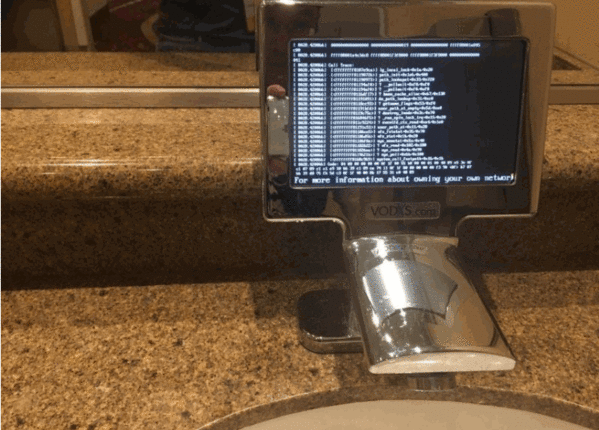
A bathroom IOT tap that has been hacked
6. Not enough people to battle the new hacking onslaught
At best the number of dedicated security personnel remains steady while the numbers of attacks increases year on year www.cisco.com/go/acr2017
A Cisco study indicates that there’s a global shortage of more than a million IT security pros, and the gap is slated to rise to as much as 1.5 million by 2019. Consequently, many organizations are faced with vacancies in critical security posts, which lead to greater vulnerabilities and higher risks of data breaches.
To end with a quote, "you better start swimmin’ or you’ll sink like a stone. For the times they are a-changin’" Bob Dylan. It's time to take security seriously.
Daniel Taylor




 502 Retweets 755 likes
502 Retweets 755 likes